Wednesday, November 14, 2012
Happy Diwali…!
Labels:
cover picture,
festival,
graphics,
greetings,
India
Sunday, October 28, 2012
creative facebook cover picture
Thursday, October 25, 2012
KITS Ramtek too got blonds!!
Monday, October 22, 2012
How to insert space in text on a NOKIA!!!
#prank
on a boring weekend night i decided to ask my online friends to help me insert spaces in texts on a nokia cellular device. here, are some of the responses that i received on facebook chat…


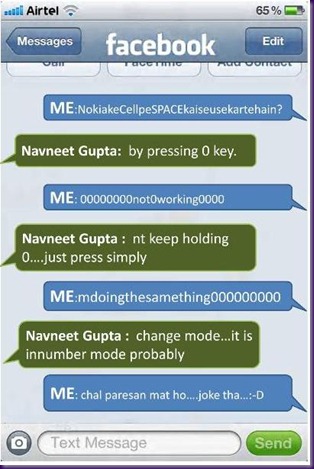

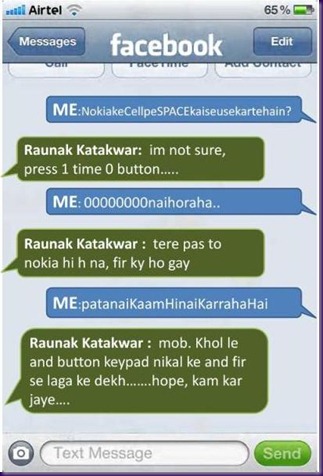


on a boring weekend night i decided to ask my online friends to help me insert spaces in texts on a nokia cellular device. here, are some of the responses that i received on facebook chat…

now when did u actually see NOKIA 3315 last time around. Lets forgive him for being samsung user.





Nokia 3351…!!!
now, how was i chatting on facebook using a 3351…
Friday, October 19, 2012
creative facebook cover picture
Thursday, June 28, 2012
ibm tgmc: project promotion video
Wednesday, June 27, 2012
Encryption: Security Sentry or Threat
Encryption: Security Sentry or Threat
Ghanshyam Verma, Mohit Choudhary
Computer Technology Dept.
KITS ramtek (Nagpur-441106)
KITS ramtek (Nagpur-441106)
ghanshyam.verma@ovi.com,
mailmohitc@yahoo.in
(paper presented at XI ANNUAL ISTE STUDENTs' CONVENTION' 2011, Maharastra-Goa Section)
Abstract— The paper “Encryption: Security Sentry or Threat” aims at
presenting the definition, introduction, overview, implementation, generic
issues related with implementation and compares the benefits of encryption with
the misuse and prices involved in the process. The paper also covers a detailed
survey of methods adopted for encryption and a case study on few widely used
encryption algorithms. The paper also looks into encryption methods adopted by
some major organisations and flaws presents in some of these algorithms. The
paper contains a detailed overview of misuse concerned with encryption by
individuals and by organisations; and overview of the value of understanding
international encryption regulation.
This abstract contains a brief layout of
actual paper and highlights the associated keywords.
Encryption is the process of transforming
information (referred to as plaintext) using an algorithm to make it unreadable
to anyone except those possessing special knowledge referred to as a key.
Decryption implicitly refers to reverse process i.e. it is used to make encrypted
information readable again.
Encryption has long been used by
militaries and governments to facilitate secret communication. Encryption is
now commonly used in protecting information within many kinds of civilian
systems. The CSI (Computer Security Institute) reported that in 2007, 71% of
companies surveyed utilized encryption for some of their data in transit, and
53% utilized encryption for some of their data in storage.
Traditionally, several methods can be
used to encrypt data streams. Encryption methods can be SYMMETRIC in which
encryption and decryption keys are the same, or ASYMMETRIC (aka 'Public Key')
in which encryption and decryption keys differ.
The Data Encryption Standard (DES) is a
block cipher that uses shared secret encryption. It was selected by the
National Bureau of Standards as an official Federal Information Processing
Standard (FIPS).
Encryption technology offers both
substantial benefits (by protecting the confidentiality, authenticity, and
integrity of business and personal information) and substantial risks (by
making it easier for criminals and terrorists to conceal communications
regarding illegal behaviour). While most countries recognize the benefits of
encryption, the associated risks have led many governments to impose controls
on the import, use, and export of encryption software, hardware and technical
information.
Transparent data encryption (TDE) is a
key-based access control system. Even if the encrypted data is retrieved, it
cannot be understood until authorized decryption occurs, which is automatic for
users authorized to access the table. This paper contains a study on TDE with
reference to oracle DB systems.
The paper contains an account of
encryption methods used by criminals and terrorists and how they use it to hide
crimes in cyberspace, along with several examples of such attacks and acts. It
also contains counter measures as suggested by various international and
national agencies.
Last but not the least it contains a
brief account on understanding the international regulations on encryption by
the organisations.
Keywords— encryption, decryption, key, signature, algorithm, plaintext,
cipher, cipertext, security, weakness, strength, statistics, symmetry,
asymmetry, PGP, RSA, EFS, request generator, ‘multi-phase’ S Table, DES, FIPS,
AES, brute force, NSA, index of coincidence, authentication, transparent data
encryption, DMH, beast, non-repudiation, strategy, regulations.
I. Encryption- an Introduction
Encryption is the process of
transforming information (referred to as plaintext) using
an algorithm (called a cipher) to make it unreadable to anyone
except those possessing special knowledge, usually referred to as a key.
The result of the process is encrypted information (in cryptography,
referred to as cipher-text). In many contexts, the
word encryption also implicitly refers to the reverse
process, decryption (e.g. “software for encryption” can typically
also perform decryption), to make the encrypted information readable again
(i.e. to make it unencrypted).
Encryption has long been used by
militaries and governments to facilitate secret communication. Encryption is
now commonly used in protecting information within many kinds of civilian
systems. For example, the Computer Security Institute reported that
in 2007, 71% of companies surveyed utilized encryption for some of their data
in transit, and 53% utilized encryption for some of their data in storage. Encryption
can be used to protect data "at rest", such as files
on computers and storage devices (e.g. USB flash drives). In
recent years there have been numerous reports of confidential data such as
customers' personal records being exposed through loss or theft of laptops or
backup drives. Encrypting such files at rest helps protect them should physical
security measures fail. Digital rights management systems which
prevent unauthorized use or reproduction of copyrighted material and protect
software against reverse engineering (see also copy protection)
are another somewhat different example of using encryption on data at rest.
Encryption is also used to protect data
in transit, for example data being transferred via networks (e.g.
the Internet, e-commerce), mobile telephones, wireless
microphones, wireless intercom systems, Bluetooth devices
and bank automatic teller machines. There have been numerous reports of
data in transit being intercepted in recent years. Encrypting data in
transit also helps to secure it as it is often difficult to physically secure
all access to networks.
Encryption, by itself, can protect the
confidentiality of messages, but other techniques are still needed to protect
the integrity and authenticity of a message; for example, verification of
a message authentication code (MAC) or a digital signature.
II. Encryption – a brief history
The earliest known use of cryptography
is found in non-standard hieroglyphs carved into monuments from Egypt’s Old
Kingdom (say 4500 years ago). These are not thought to be serious attempts at
secret communications, however, but rather to have been attempts at mystery,
intrigue, or even amusement for literate onlookers. These are examples of still
another use of cryptography, or of something that looks (impressively if
misleadingly) like it. Later, Hebrew scholars made use of simple Substitution
ciphers (such as the Atbash cipher) beginning perhaps around 500 to 600 BCE.
Cryptography has a long tradition in religious writing likely to offend the
dominant culture or political authorities. Perhaps the most famous is the
‘Number of the Beast’ from the book of Revelations in the Christian New Testament.
‘666’ is almost certainly a cryptographic (i.e., encrypted) way of concealing a
dangerous reference: many scholars believe it’s a concealed reference to the
Roman Empire, or the Emperor Nero. (and so to Roman policies of persecution of
Christians) that would have been understood by the initiated (who ‘had the
codebook’), and yet be safe (or at least somewhat deniable and so less
dangerous) if it came to the attention of the authorities. In Europe during and after the Renaissance,
citizens of the various Italian states, including the Papacy, were responsible
for substantial improvements in cryptographic practice (e.g. polyalphabetic
ciphers invented by Leon Alberti ca 1465). And in the Arab world, religiously
motivated textual analysis of the Koran led to the invention of the frequency
analysis technique for breaking monoalphahetic substitution cyphers sometime
around 1000 CE.
Mathematical cryptography leapt ahead
(also secretly) after World War I. Marian Rejewski, in Poland, attacked and
‘broke’ the early German Army Enigma system (an electromechanical rotor cipher
machine) using theoretical matheniatics in 1932. The break continued up to ’39,
when changes in the way the German Armys Enigma machines were used required
more resources than the Poles could deploy. His work was extended by Alan
Turing, Gordon Welchman and others at Bletchley Park beginning in 1939, leading
to sustained breaks into several others of the Enigma variants and the assorted
networks for which they were used. US Navy cryptographers (with cooperation
from British and Dutch cryptographers after 1940) broke into several Japanese
Navy crypto systems. The break into one of them famously led to the US victory
in the Battle of Midway. An US Army group the SIS, managed to break the highest
security Japanese diplomatic cipher system (an electromechanical ‘stepping
switch’ machine called Purple by the Americans) even before WW-II began.
By World War II mechanical and
electromechanical cryptographic cipher machines were in wide use, but they were
impractical manual systems. Great advances were made in both practical and
mathematical cryptography in this period, all in secrecy.
The era of modem cryptography really
begins with Claude Shannon, arguably the father of mathematical cryptography.
In 1949 he published the paper Communication l’heory of Secrecy Systems in the
Bell System Technical Journal, and a little later the book Mathematical Theory
of Communication with Warren Weaver.
1969 saw two major public (i.e.. non-secret)
advances. First was the DES (Data Encryption Standard) submitted by IBM, at the
invitation of the National Bureau of Standards (now NIST), in an effort to
develop secure electronic communication facilities for businesses such as banks
and other large financial organizations.
In recent years public disclosure of
secret documents held by the UK government has shown that asymmetric key
cryptography, D-H key exchange, and the best known of the public key / private
key algorithms (i.e., what is usually called the RSA algorithm), all seem to
have been developed at a UK intelligence agency before the public announcement
by Diffie and Hellman in ‘76. GCI-IQ has released documents claiming that they
had developed public key cryptography before the publication of Diffie and
Hellman’s paper. Various classified papers were written at GCHQ during the 1960s
and 1970s which eventually led to schemes essentially identical to RSA
encryption and to Diffie-Hellman key exchange in 1973 and 1974. Some of these
have now been published, and the inventors (James Ellis, Clifford Cocks, and
Malcolm Williamson) have made public (some of) their work and stuff.
III. Some encryption methods
Traditionally, several methods can be
used to encrypt data streams, all of which can easily be implemented through
software, but not so easily decrypted when either the original or its encrypted
data stream are unavailable. (When both source and encrypted data are
available, code-breaking becomes much simpler, though it is not necessarily
easy). The best encryption methods have little effect on system performance,
and may contain other benefits (such as data compression) built in. For e.g. the
well-known 'PKZIP®' utility offers both compression and data encryption in this
manner.
Encryption methods can
be SYMMETRIC in which encryption and decryption keys are the same,
or ASYMMETRIC (aka 'Public Key') in which encryption and decryption
keys differ. 'Public Key' methods must be asymmetric, to the extent that the
decryption key CANNOT be easily derived from the encryption key. Symmetric
keys, however, usually encrypt more efficiently, so they lend themselves to
encrypting large amounts of data.
Asymmetric encryption is often limited
to ONLY encrypting symmetric key and other information that is needed in order
to decrypt a data stream, and the remainder of the encrypted data uses the
symmetric key method for performance reasons. This does not in any way diminish
the security nor the ability to use a public key to encrypt the data, since the
symmetric key method is likely to be even MORE secure than the asymmetric
method.
Further for symmetric key ciphers,
there are basically two types: BLOCK CIPHERS, in which a fixed length block is
encrypted, and STREAM CIPHERS, in which the data is encrypted one 'data unit'
(typically 1 byte) at a time, in the same order it was received in.
Fortunately, the simplest of all of the
symmetric key 'stream cipher' methods is the TRANSLATION TABLE (or 'S table'),
which should easily meet the performance requirements of even the most
performance-intensive application that requires data to be encrypted. In a
translation table, each 'chunk' of data (usually 1 byte) is used as an offset
within one or more arrays, and the resulting 'translated' value is then written
into the output stream. While translation tables are very simple and fast, the
down side is that once the translation table is known, the code is broken.
Further, such a method is relatively straightforward for code breakers to
decipher - such code methods have been used for years, even before the advent
of the computer. Still, for general "unreadability" of encoded data,
without adverse effects on performance, the 'translation table' method lends
itself well.
One very important feature of a good
encryption scheme is the ability to specify a 'key' or 'password' of some kind,
and have the encryption method alter itself such that each 'key' or 'password'
produces a unique encrypted output, one that also requires a unique 'key' or
'password' to decrypt. This can either be a symmetric or asymmetric key. The
popular 'PGP' public key encryption, and the 'RSA' encryption that it's based
on, uses an 'asymmetrical' key, allowing you to share the 'public' encryption
key with everyone, while keeping the 'private' decryption key safe. The
encryption key is significantly different from the decryption key, such that
attempting to derive the private key from the public key involves too many
hours of computing time to be practical. It would NOT be impossible, just
highly unlikely, which is 'pretty good'.
Let’s look into some of the famous
encryption algorithms for a better understanding of the encryption.
A. RSA
In 1977, shortly after the idea of a
public key system was proposed, three mathematicians, Ron Rivest, Adi Shamir
and Len Adleman gave a concrete example of how such a method could be
implemented. To honour them, the method was referred to as the RSA Scheme. The
system uses a private and a public key. To start two large prime numbers are
selected and then multiplied together; n=p*q.
If we let f(n) = (p-1) (q-1), and
e>1 such that GCD(e, f(n))=1. Here e will have a fairly large probability of
being co-prime to f(n), if n is large enough and e will be part of the
encryption key. If we solve the Linear Diophantine equation; ed congruent 1 (mod
f(n)), for d. The pair of integers (e, n)are the public key and (d, n) form the
private key. Encryption of M can be accomplished by the following expression;
Me = qn + C where 0<= C < n. Decryption would be the inverse of the
encryption and could be expressed as; Cd congruent R (mod n) where 0<= R
< n. RSA is the most popular method for public key encryption and digital
signatures today.
B. DES/3DES
The Data Encryption Standard (DES) was
developed and endorsed by the U.S. government in 1977 as an official standard
and forms the basis not only for the Automatic Teller Machines (ATM) PIN
authentication but a variant is also utilized in UNIX password encryption. DES
is a block cipher with 64-bit block size that uses 56-bit keys. Due to recent
advances in computer technology, some experts no longer consider DES secure
against all attacks; since then Triple-DES (3DES) has emerged as a stronger
method. Using standard DES encryption, Triple-DES encrypts data three times and
uses a different key for at least one of the three passes giving it a
cumulative key size of 112-168 bits.
C. BLOWFISH
Blowfish is a symmetric block cipher
just like DES or IDEA. It takes a variable-length key, from 32 to 448 bits,
making it ideal for both domestic and exportable use. Bruce Schneier designed
Blowfish in 1993 as a fast, free alternative to the then existing encryption
algorithms. Since then Blowfish has been analyzed considerably, and is gaining
acceptance as a strong encryption algorithm.
D. IDEA
International Data Encryption Algorithm
(IDEA) is an algorithm that was developed by Dr. X. Lai and Prof. J. Massey in
Switzerland in the early 1990s to replace the DES standard. It uses the same
key for encryption and decryption, like DES operating on 8 bytes at a time.
Unlike DES though it uses a 128 bit key. This key length makes it impossible to
break by simply trying every key, and no other means of attack is known. It is
a fast algorithm, and has also been implemented in hardware chipsets, making it
even faster.
E. SEAL
Rogaway and Coppersmith designed the
Software-optimized Encryption Algorithm (SEAL) in 1993. It is a Stream-Cipher,
i.e., data to be encrypted is continuously encrypted. Stream Ciphers are much
faster than block ciphers (Blowfish, IDEA, DES) but have a longer
initialization phase during which a large set of tables is done using the
Secure Hash Algorithm. SEAL uses a 160 bit key for encryption and is considered
very safe.
F. RC4
RC4 is a cipher invented by Ron Rivest,
co-inventor of the RSA Scheme. It is used in a number of commercial systems
like Lotus Notes and Netscape. It is a cipher with a key size of up to 2048
bits (256 bytes), which on the brief examination given it over the past year or
so seems to be a relatively fast and strong cipher. It creates a stream of
random bytes and 'XORing' those bytes with the text. It is useful in situations
in which a new key can be chosen for each message.
IV. A detailed study of encryption method used in oracle db
This study was made to get a clear
insight into encryption methodology. Oracle Database uses authentication,
authorization, and auditing mechanisms to secure data in the database, but not
in the operating system data files where data is stored. To protect these data
files, Oracle Database provides transparent data encryption.
Transparent data encryption is a
key-based access control system. Even if the encrypted data is retrieved, it
cannot be understood until authorized decryption occurs, which is automatic for
users authorized to access the table.
When a table contains encrypted columns,
a single key is used regardless of the number of encrypted columns. This key is
called the column encryption key. The column encryption keys for all tables,
containing encrypted columns, are encrypted with the database server master
encryption key and stored in a dictionary table in the database. No keys are
stored in the clear.
As shown in Figure below, the
master encryption key is stored in an external security module that is outside
the database and accessible only to the security administrator. For this
external security module, Oracle uses an Oracle wallet as described in this
chapter. Storing the master encryption key in this way prevents its
unauthorized use.
 |
| Fig. 1. Showing basic modules of Transparent Data Encryption as used in ORACLE® DB. |
A Overview of the Transparent Data Encryption as used in Oracle DB
To enable transparent data encryption,
you must have the ALTER SYSTEM privilege and a valid password to the
Oracle wallet. If an Oracle wallet does not exist, then a new one is created
using the password specified in the SQL command.
To create a new master key and begin
using transparent data encryption, issue the following command:
ALTER SYSTEM SET ENCRYPTION KEY
IDENTIFIED BY password
Enclose the password in
double quotation marks (" "). This command generates the database
server master encryption key, which the server uses to encrypt the column
encryption key for each table. No table columns in the database can be
encrypted until the master key of the server has been set.
The master encryption key remains
accessible to the database until the database instance is shutdown. To load the
master encryption key after the database is restarted, use the following
command:
ALTER SYSTEM SET ENCRYPTION WALLET OPEN
IDENTIFIED BY password
Enclose the password in double
quotation marks (" "). To create a new table with encrypted columns,
use the CREATE TABLE command in the following form:
CREATE TABLE table_name ( column_name
column_type ENCRYPT,....);
The ENCRYPT keyword against a
column specifies that the column should be encrypted.
If an existing table has columns that
require encryption, then use the ALTER TABLE command in the following
form:
ALTER TABLE table_name MODIFY (
column_name column_type ENCRYPT,...);
The ENCRYPT keyword against a
column specifies that the column should be encrypted.
To disable access to all encrypted
columns in the database, use the following command:
ALTER SYSTEM SET ENCRYPTION WALLET
CLOSE
The preceding
command disables access to the master key in the wallet and prevents access to
data in the encrypted columns. You need to open the wallet again, using
the
ALTER SYSTEM
SET WALLET OPEN IDENTIFIED BY password
to re-enable
access to the master encryption key.
V. Self tutorials to design private encrypter
Based on our understanding of various
algorithms, methodologies and processes we may conclude that designing and implementing
an encrypter is extremely easy. All one need is to have is some basic
programming skills and a sound knowledge to work with different databases.
There are many online tutorials and web-pages available that provides encrypter
designing techniques. In fact many such sites provide ready to use codes to
built and implement private encrypter.
We encountered few such method of building ciphers online. Here is an
example, we found on following address: [http://hackguide4u.blogspot.com/2011/01/how-to-make-crypter.html].
The stated example showed development of an encrypter using an existing RC4
module on VB6 platform.
The above example shows how simple it
is to make a private encrypter for the individuals say script kiddies. Such
technologies in wrong hands can be fatal to cyber security. Let’s have a walk
through some of the major cyber thefts and misconducts.
VI. encryption: Demonic face
Despite being a revolutionary blessing
the encryption has been long used by individuals and organisations for personal
benefits/ spreading cyber terror/ hiding crime evidences. As sometimes happens,
what at first glance seems to be
a great idea can
actually do more
harm than good.
Encryption is being used as a tool for
hiding information in a variety of crimes, including fraud and other financial
crimes, theft of proprietary information, computer crime, drugs, child
pornography, terrorism, murder, and economic and military espionage. We have
not heard about many cases where criminals exploited weak encryption systems to
their advantage, for example, to steal proprietary information. However, a
British blackmailer intercepted encrypted transactions transmitted by a bank in
the U.K. After breaking the code, he successfully extorted 350,000 from the
bank and several customers by threatening to reveal the information to the
Inland Revenue.
Here are few cases involving
encryption:
Aum
Shinri Kyo (Supreme Truth): On March 20, 1995, the
Aum Supreme Truth cult dropped bags of sarin nerve gas in the Tokyo subway,
killing 12 people and injuring 6,000 more [Kaplan & Marshall 96]. They had
developed a variety of weapons of mass destruction, both chemical (sarin, VX,
mustard gas, cyanide) and biological (botulism, anthrax, Q fever). They were
attempting to develop a nuclear capability and a "death ray" that
could destroy all life. Shoko Asahara and his followers used murder,
kidnapings, extortion, torture, poison, electric shocks, drugs, imprisonment,
and wiretaps to acquire assets, control defections, and attack their enemies.
Among the tens of thousands of members were some of Japan's brightest
scientists and doctors. The cult had stored their records on computers,
encrypted with RSA. Authorities were able to decrypt the files after finding
the key on a floppy disk. The encrypted files contained evidence that was
crucial to the investigation, including plans and intentions to deploy weapons
of mass destruction in Japan and the United States.
New
York Subway Bomber: In 1995, John Lucich was
assigned to the Manhattan District Attorney's Office to assist with the
investigation of the New York subway bomber, Mr. Leary. Mr. Leary was
eventually found guilty and sentenced to 94 years in jail for setting off fire
bombs in the New York subway system. He had applied his own form of encryption
to numerous files on his computer, and Mr. Lucich was given the computers for
analysis. After failing to break the encryption themselves, the files were sent
to outside encryption experts. These efforts also failed. Eventually, the
encryption was broken by a federal agency. The files contained child
pornography and personal information, which was not particularly useful to the
case. However, investigators retrieved other evidence from the computer that
was used at trial.
Multi-site
gambling enterprise: A significant gambling
enterprise operated multiple sites linked by a computer system, with drop-offs
and pick-ups spanning three California counties. The head of the enterprise
managed his records with a commercial accounting program, using a codeword to
encrypt the files. The software manufacturer refused to assist law enforcement
in breaking the code. However, the police were able to crack the codeword by
exploiting weaknesses in the system. The encrypted files contained the daily
take on the bets, pay-offs, persons involved, amounts due and paid or owed, and
so forth. After breaking the code, they printed the results of four years of
bookmaking, which resulted in a plea of guilty to the original charges and a
sizeable payment of back taxes, both state and federal.
Aldrich
Ames spy case: Ames was a CIA agent eventually
convicted of espionage against the United States. He had encrypted his computer
files using standard commercial off-the-shelf software. The investigator
handling the computer evidence was able to decrypt the files using software
supplied by Access Data Corporation [Thompson 97]. Failure to recover the
encrypted data would have weakened the case.
Kevin
Poulson: Kevin Poulson was a skilled hacker who
rigged radio giveaways, "winning" Porsches, trips to Hawaii, and tens
of thousands of dollars in computer cash. He also burglarized telephone
switching offices and hacked his way into the telephone network in order to
determine who was being wiretapped and to install his own. In his book about
Poulson's crime spree, Jonathan Littman reported that Poulson had encrypted
files documenting everything from the wiretaps he had discovered to the
dossiers he had compiled about his enemies [Littman 97]. The files were said to
have been encrypted several times using the "Defense Encryption
Standard" [sic]. According to Littman, a Department of Energy
supercomputer was used to find the key, a task which took several months at an
estimated cost of hundreds of thousands of dollars. The result yielded nearly
ten thousand pages of evidence.
As in examples above, encryption has
been used of in better stated misused across the timeline. Yet, encryption has
become an in-separable part of our cyber life. We have discussed the benefits
associated with encryption in upcoming section.
VII. encryption: angelic face
Encryption plays a vital role in data
safety. It has been a trusted companion for the following reasons:
Companies often possess data files on
employees which are confidential, such as medical records, salary records, etc.
Employees will feel safer knowing that these files are encrypted and are not
accessible to casual inspection by data entry clerks.
Individuals may share working space
with others, of whose honor they are not entirely sure, and may wish to make
certain that in their absence no-one will find anything by snooping about in
their hard disk.
A company may wish to transfer sensitive
business information between sites such as branch offices. Or it may wish to
send confidential information (for example, a negotiating position, operating
procedures or proprietary data) to an agent in the field (perhaps abroad). If
the information is encrypted before transmission then one does not have to
worry about it being intercepted since if this happens the encrypted data is
incomprehensible (without the encryption key).
A company may have information that a
competitor would like to see, such as information concerning legal or financial
problems, results of research, who the customers are and what they are buying,
information revealing violations of government regulations, secret formulas or
details of manufacturing processes, plans for future expansion or for the development
of new products.
A person or company may wish to
transport to a distant location a computer which contains sensitive information
without being concerned that if the computer is examined en route (e.g. by
foreign customs agents) then the information will be revealed.
Two individuals may wish to correspond
by email on matters that they wish to keep private and be sure that no-one else
is reading their mail.
From above example, it is clear
encryption is used in two general cases:
(a) When information, once encrypted,
is simply to be stored on-site (and invulnerable to unauthorized access) until
there is a need to access that information.
(b) When information is to be
transmitted somewhere and it is encrypted so that if it is intercepted before
reaching its intended destination the interceptor will not find anything they
can make sense of.
VIII. debate- is encryption sentry or threat?
A major ongoing debate related to
terrorism and the Internet is the question of encryption. On the one hand,
encryption protects individual and corporate privacy and is a fundamental
building block of electronic commerce. On the other hand, police and
intelligence agencies oppose denying the government access to electronic
information because terrorists and other criminals can use encryption
technology to conduct illegal activities while avoiding government monitoring.
World Trade Center bombing mastermind, Ramzi Ahmed Yousef, for example,
utilized encryption technology in his foiled plot to blow up 11 U.S. airliners
in the Far East.
Writing in The Journal of
Information Policy, Attorney General Janet Reno said, "The potential harm
to public safety and national security from the widespread distribution of
encryption is already apparent. We have begun to encounter encryption in
criminal cases. More and more frequently, criminals are encrypting data on
their computers.... Terrorists in New York City were plotting to bomb the
United Nations Building, the Lincoln and Holland Tunnels, and the main federal
building. Court-ordered electronic surveillance enabled the FBI to disrupt the
plot, and the evidence obtained was used to convict the conspirators.... We
must work quickly, and together, to develop global solutions that will promote
privacy and commerce, yet protect us all."
IX. conclusion
“‘Ban cryptography! Yes. Let’s also ban
pencils, pens and paper, since criminals can use them to draw plan of the joint
they are cashing or even, god forbid, create one time pads to pass un-crack
able codes to each other. Ban open spaces since criminals could use them to
converse with each other out of earshot of the police. Let’s ban flags since
they could be used to pass secret messages in semaphore. In fact let’s just ban
all form of verbal and non-verbal communication — let’s see those criminals
make plans now!” – Anonymous.
Anonymously said, still concludes and
describes the debate very clearly. We cannot let go of a technology just
because it could be put to misuse.
References
[1]
http://www3.edgrnet.net/dcowley/doc.html
[2] http://citeseer.nj.nec.com/340126.html
[3] http://www.adl.org/terror/focus/16_focus_a4.asp
[4] http://www.hermetic.ch/crypto/intro.htm
[5] http://en.wikipedia.org/wiki/Encryption
[6] http://www.mrp3.com/encrypt.html
[7] http://cryptome.org/hiding-db.htm
[8] http://personal.law.miami.edu/~froomkin/articles/herald.html
[9] http://docs.oracle.com/cd/B28359_01/~/asotrans.htm
[10] http://www.cs.georgetown.edu/~denning/crypto/cases.htm
Friday, April 27, 2012
Thursday, April 12, 2012
IETE Students' Forum : Farewell
great is the art of beginning, but greater is the art of ending.
miss u all...
watch this video on Youtube! click here.
teknodeon 2k12 : t-shirt.
Subscribe to:
Comments (Atom)











